안녕하세요.
오늘은 Juniper SRX Firmware Upgrade를 해보겠습니다.
Juniper SRX는 보통 CLI에서 많이 사용 합니다.
1. Juniper 기본 설정값을 확인 합니다.
| root> show configuration | display set | no-more set version 21.4R3-S3.4 set system root-authentication encrypted-password "$6$Kt3WFIik$0vN75BKuEZDkbTiLXUiAaTbrdkZ2EQCMo0u/G2D.nI3yQFDnN2sRwSwMra/BrVBfXg2lnWtzltwnPZkIWY2Zi." set system services ssh set system services netconf ssh set system services dhcp-local-server group jdhcp-group interface irb.0 set system services web-management https system-generated-certificate set system name-server 8.8.8.8 set system name-server 8.8.4.4 set system syslog archive size 100k set system syslog archive files 3 set system syslog user * any emergency set system syslog file interactive-commands interactive-commands any set system syslog file messages any notice set system syslog file messages authorization info set system max-configurations-on-flash 5 set system max-configuration-rollbacks 5 set system license autoupdate url https://ae1.juniper.net/junos/key_retrieval set system phone-home server https://redirect.juniper.net set system phone-home rfc-compliant set security screen ids-option untrust-screen icmp ping-death set security screen ids-option untrust-screen ip source-route-option set security screen ids-option untrust-screen ip tear-drop set security screen ids-option untrust-screen tcp syn-flood alarm-threshold 1024 set security screen ids-option untrust-screen tcp syn-flood attack-threshold 200 set security screen ids-option untrust-screen tcp syn-flood source-threshold 1024 set security screen ids-option untrust-screen tcp syn-flood destination-threshold 2048 set security screen ids-option untrust-screen tcp syn-flood timeout 20 set security screen ids-option untrust-screen tcp land set security nat source rule-set trust-to-untrust from zone trust set security nat source rule-set trust-to-untrust to zone untrust set security nat source rule-set trust-to-untrust rule source-nat-rule match source-address 0.0.0.0/0 set security nat source rule-set trust-to-untrust rule source-nat-rule then source-nat interface set security policies from-zone trust to-zone trust policy trust-to-trust match source-address any set security policies from-zone trust to-zone trust policy trust-to-trust match destination-address any set security policies from-zone trust to-zone trust policy trust-to-trust match application any set security policies from-zone trust to-zone trust policy trust-to-trust then permit set security policies from-zone trust to-zone untrust policy trust-to-untrust match source-address any set security policies from-zone trust to-zone untrust policy trust-to-untrust match destination-address any set security policies from-zone trust to-zone untrust policy trust-to-untrust match application any set security policies from-zone trust to-zone untrust policy trust-to-untrust then permit set security policies pre-id-default-policy then log session-close set security zones security-zone trust host-inbound-traffic system-services all set security zones security-zone trust host-inbound-traffic protocols all set security zones security-zone trust interfaces irb.0 set security zones security-zone untrust screen untrust-screen set security zones security-zone untrust interfaces ge-0/0/0.0 host-inbound-traffic system-services dhcp set security zones security-zone untrust interfaces ge-0/0/0.0 host-inbound-traffic system-services tftp set security zones security-zone untrust interfaces ge-0/0/0.0 host-inbound-traffic system-services https set security zones security-zone untrust interfaces ge-0/0/7.0 host-inbound-traffic system-services dhcp set security zones security-zone untrust interfaces ge-0/0/7.0 host-inbound-traffic system-services tftp set security zones security-zone untrust interfaces dl0.0 host-inbound-traffic system-services tftp set interfaces ge-0/0/0 unit 0 family inet dhcp vendor-id Juniper-srx320 set interfaces ge-0/0/1 unit 0 family ethernet-switching vlan members vlan-trust set interfaces ge-0/0/2 unit 0 family ethernet-switching vlan members vlan-trust set interfaces ge-0/0/3 unit 0 family ethernet-switching vlan members vlan-trust set interfaces ge-0/0/4 unit 0 family ethernet-switching vlan members vlan-trust set interfaces ge-0/0/5 unit 0 family ethernet-switching vlan members vlan-trust set interfaces ge-0/0/6 unit 0 family ethernet-switching vlan members vlan-trust set interfaces ge-0/0/7 unit 0 family inet dhcp vendor-id Juniper-srx320 set interfaces cl-1/0/0 dialer-options pool 1 priority 100 set interfaces dl0 unit 0 family inet negotiate-address set interfaces dl0 unit 0 family inet6 negotiate-address set interfaces dl0 unit 0 dialer-options pool 1 set interfaces dl0 unit 0 dialer-options dial-string 1234 set interfaces dl0 unit 0 dialer-options always-on set interfaces irb unit 0 family inet address 192.168.1.1/24 set access address-assignment pool junosDHCPPool family inet network 192.168.1.0/24 set access address-assignment pool junosDHCPPool family inet range junosRange low 192.168.1.2 set access address-assignment pool junosDHCPPool family inet range junosRange high 192.168.1.254 set access address-assignment pool junosDHCPPool family inet dhcp-attributes router 192.168.1.1 set access address-assignment pool junosDHCPPool family inet dhcp-attributes propagate-settings ge-0/0/0.0 set vlans vlan-trust vlan-id 3 set vlans vlan-trust l3-interface irb.0 set protocols l2-learning global-mode switching set protocols rstp interface all root> root> show system license License usage: Licenses Licenses Licenses Expiry Feature name used installed needed idp-sig 0 1 0 2030-01-26 00:00:00 UTC remote-access-ipsec-vpn-client 0 2 0 permanent remote-access-juniper-std 0 2 0 permanent Licenses installed: License identifier: JUNOS422937473 License version: 4 Valid for device: CW4024AX0159 Customer ID: KDDI ASIA PACIFIC PTE. LTD. Features: idp-sig - IDP Signature date-based, 2024-12-27 00:00:00 UTC - 2030-01-26 00:00:00 UTC root> root> show version Model: srx320 Junos: 21.4R3-S3.4 JUNOS Software Release [21.4R3-S3.4] |
2. UTP 케이블을 노트북과 Juniper SRX Ge-0/0/3에 연결합니다.
그리고 노트북에 192.168.1.2 255.255.255.0 설정하고
Ping 192.168.1.1
| C:\Users\admin>ping 192.168.1.1 Pinging 192.168.1.1 with 32 bytes of data: Reply from 192.168.1.1: bytes=32 time=1ms TTL=64 Reply from 192.168.1.1: bytes=32 time=1ms TTL=64 Reply from 192.168.1.1: bytes=32 time=2ms TTL=64 Reply from 192.168.1.1: bytes=32 time=1ms TTL=64 Ping statistics for 192.168.1.1: Packets: Sent = 4, Received = 4, Lost = 0 (0% loss), Approximate round trip times in milli-seconds: Minimum = 1ms, Maximum = 2ms, Average = 1ms C:\Users\admin> C:\Users\admin> |
3. ftp enable 합니다.
| root# set system services ftp [edit] root# show system services ftp; ssh; netconf { ssh; } dhcp-local-server { group jdhcp-group { interface irb.0; } } web-management { https { system-generated-certificate; } } [edit] root# commit commit complete [edit] root# |
또는 GUI에서 아래와 같이 확인 가능 합니다.
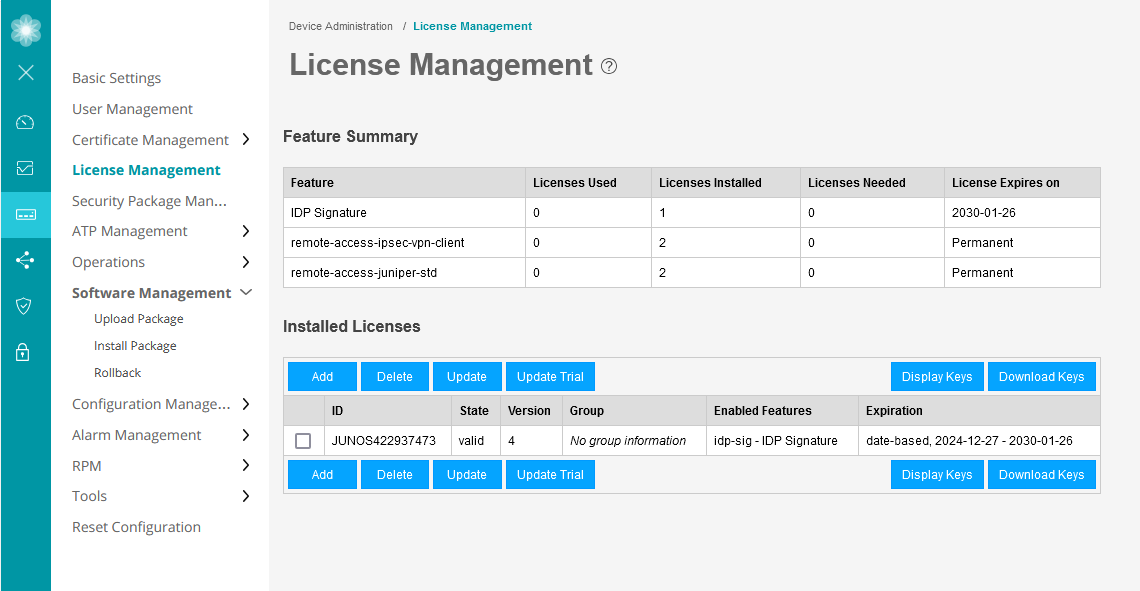
라이센스 정보 확인 합니다.
현재 SRX320 Firmware Version 확인
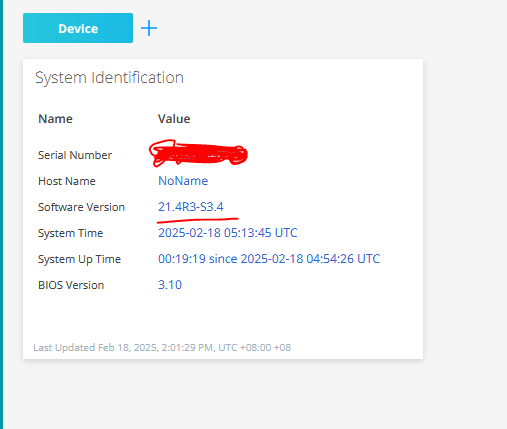
Currnet Version: 21.4R3-S3.4
Target Version: 23.4R2-S3
Firmware Upgrade Path
https://supportportal.juniper.net/s/article/Junos-upgrade-paths-for-SRX-platforms?language=en_US
CEC Juniper Community
supportportal.juniper.net
Upgrade table
To make it easy to lookup for each Junos release for SRX from which earlier releases it is supported to directly upgrade to it, please see the below table.
Before performing the upgrade, please make sure to check the Notes section below for possible caveats and limitations which may apply.
Target Junos releaseDirect upgrade supported from
| 24.4(*2) | 24.2, 23.4, 23.2 |
| 24.2 | 23.4, 23.2, 22.4 |
| 23.4 | 23.2, 22.4, 22.3 |
| 23.2 | 22.4, 22.3, 22.2 |
| 22.4 | 22.3, 22.2, 22.1, 21.4 |
| 22.3 | 22.2, 22.1, 21.4 |
| 22.2 | 22.1, 21.4, 21.3, 21.2 |
| 22.1 | 21.4, 21.3, 21.2 |
| 21.4 | 21.3, 21.2, 21.1, 20.4 |
| 21.3 | 21.2, 21.1, 20.4 |
| 21.2 | 21.1, 20.4, 20.3, 20.2 |
| 21.1 | 20.4, 20.3, 20.2 |
| 20.4 | 20.3, 20.2, 20.1, 19.4 |
| 20.3 | 20.2, 20.1, 19.4 |
| 20.2 | 20.1, 19.4, 19.3, 19.2 |
| 20.1 | 19.4, 19.3, 19.2 |
| 19.4 | 19.3, 19.2, 19.1, 18.4, 15.1X49 |
| 19.3 | 19.2, 19.1, 18.4 |
| 19.2 | 19.1, 18.4, 18.3, 18.2 |
| 19.1 | 18.4, 18.3, 18.2 |
| 18.4 | 18.3, 18.2, 18.1, 17.4, 15.1X49 |
| 18.3 | 18.2, 18.1, 17.4 |
| 18.2 | 18.1, 17.4, 17.3 |
| 18.1 | 17.4, 17.3 |
| 17.4 | 17.3, 15.1X49 |
| 17.3 | 15.1X49 |
| 15.1X49 | 12.3X48 |
위에 정보를 확인한 결과
To upgrade your SRX device from Junos 21.4R3 to 23.4R2-S3
Path: 21.4R3 --> 22.4R3 --> 23.4R2-S3
Juniper 홈페이지에 접속해서 Firmware를 다운로드 합니다.
https://support.juniper.net/support/downloads/?p=srx320
Downloads
Help us improve your experience. Let us know what you think. Do you have time for a two-minute survey?
support.juniper.net
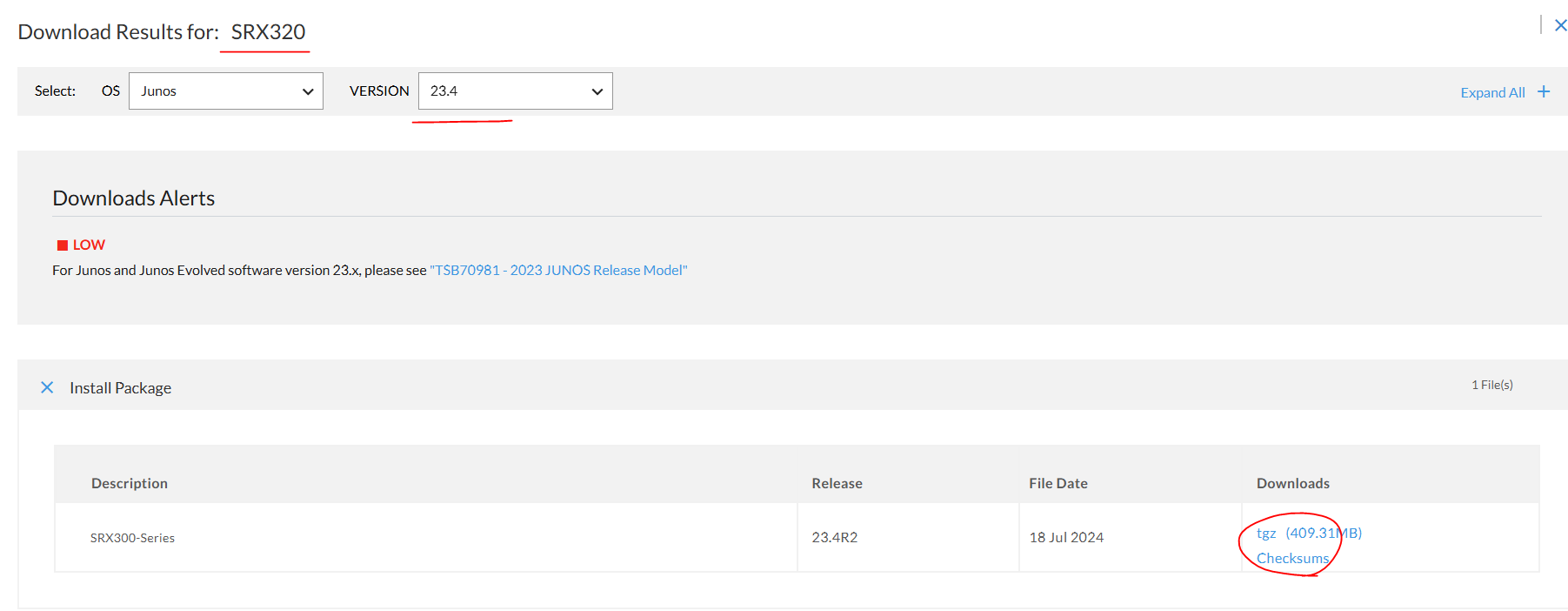

22.4R3.25 - Checksums 정보
MD5 : 22c2f625180aabe85f252f89c3f212d3
SHA1 : 6e5b2d2ef96227b1db95d265ba899854bd1b6c24
SHA256 : 12d7f2b8245c3f6610f34380a57a642d831aba83f6008b6929d3987737f93bf7
SHA512 : 024fd745d0d3e53daee5713e11aab9029ca9f9979d9b677be8e45f93446e7c2d0b228535291acdec9b3007d51f396ddd407786921cbd99be070212359edebfda
23.4R2.13 - Checksums 정보
MD5 : 18085ebeec8305f538226bd690b18954
SHA1 : 9eaa6ba139907f30863e8a53f9641ad206078d5e
SHA256 : 0728b9bf9c1576661b325a12d0fac7b5c3c2dd29dce184b9bcefca5ca4d973f8
SHA512 : 29d7c7676ca0bd8d8813f6ac2205eaf834ff0e7998ae7ff078f609630131c0136c105128707508e76e9b566ade07230af41256e6fcb0380b3977ea9a52bfdb06
Firmware업르게이드 하기전에 모든 Firmware Version를 다운로드 받았습니다.
winscp를 실행 합니다.
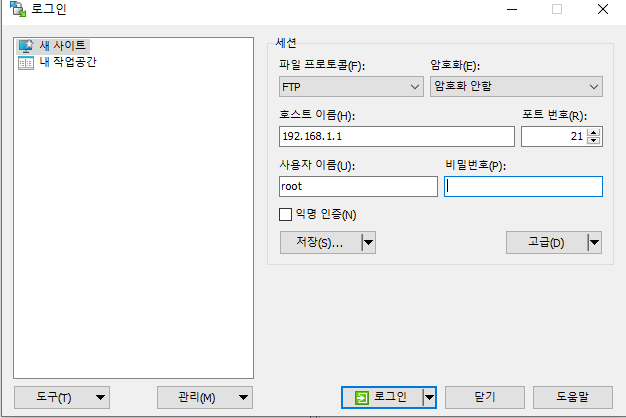
접속이 완료 되면 경로를 아래와 같이 합니다.

첫번째 이미지를 업로드 합니다.

파일이 업로드가 완료 되면 아래와 같이 명령어를 입력해서 확인 합니다.
| root> file list /cf/var/tmp /cf/var/tmp: appidd_cust_app_trace appidd_trace_debug bcast.bdisp.log bcast.disp.log bcast.rstdisp.log bcast.undisp.log cleanup-pkgs.log ebmq_authd_vty eedebug_bin_file install/ junos-srxsme-22.4R3.25.tgz kmdchk.log krt_rpf_filter.txt mmcq_authd mmcq_bbeStatsdGetCollector mmcq_mmdb_rep_mmcq mmcq_sdb_bbe_mmcq nsd_restart pfe-limit pfe_debug_commands phone-home/ pics/ policy_status rtsdb/ sd-upgrade/ sec-download/ vi.recover/ root> |
Firmware MD5 checksum 확인
| root> file checksum md5 /cf/var/tmp/junos-srxsme-22.4R3.25.tgz MD5 (/cf/var/tmp/junos-srxsme-22.4R3.25.tgz) = 22c2f625180aabe85f252f89c3f212d3 root> |
1차로 21.4R3-S3.4 -> 22.4R3.25 업그레이드
아래처럼 입력 하고 업그레이드가 완료 될때가지 기다립니다.
| root> request system software add /cf/var/tmp/junos-srxsme-22.4R3.25.tgz no-validate reboot Formatting alternate root (/dev/da0s2a)... /dev/da0s2a: 596.0MB (1220680 sectors) block size 16384, fragment size 2048 using 4 cylinder groups of 149.02MB, 9537 blks, 19200 inodes. super-block backups (for fsck -b #) at: 32, 305216, 610400, 915584 saving package file in /var/sw/pkg ... Installing package '/altroot/cf/packages/install-tmp/junos-22.4R3.25' ... Verified junos-boot-srxsme-22.4R3.25.tgz signed by PackageProductionECP256_2024 method ECDSA256+SHA256 Verified junos-srxsme-22.4R3.25-domestic signed by PackageProductionECP256_2024 method ECDSA256+SHA256 Verified manifest signed by PackageProductionECP256_2024 method ECDSA256+SHA256 JUNOS 22.4R3.25 will become active at next reboot Saving state for rollback ... Rebooting ... shutdown: [pid 6825] Shutdown NOW! *** FINAL System shutdown message from root@ *** System going down IMMEDIATELY 부팅 과정 생략 Amnesiac (ttyu0) login: |
부팅이 완료 되면 로그인 합니다.
| root> show version Model: srx320 Junos: 22.4R3.25 JUNOS Software Release [22.4R3.25] root> show system license License usage: Licenses Licenses Licenses Feature Feature Feature Feature name used installed needed Expiry idp-sig 0 1 0 2030-01 -26 00:00:00 UTC remote-access-ipsec-vpn-client 0 2 0 permane nt remote-access-juniper-std 0 2 0 permane nt Licenses installed: License identifier: License version: 4 Valid for device: Customer ID: Features: idp-sig - IDP Signature date-based, 2024-12-27 00:00:00 UTC - 2030-01-26 00:00:00 UTC root> |
1차로 21.4R3-S3.4 -> 22.4R3.25 업그레이드 완료 되었습니다.
2차로 22.4R3.25 -> 23.4R2.13 업그레이드를 하겠습니다.
우선 파일을 srx에 업로드 합니다.

| root> file list /cf/var/tmp /cf/var/tmp: appidd_cust_app_trace appidd_trace_debug bcast.bdisp.log bcast.disp.log bcast.rstdisp.log bcast.undisp.log cleanup-pkgs.log dyn_filterd_trace_debug ebmq_authd_vty eedebug_bin_file install/ junos-srxsme-22.4R3.25.tgz junos-srxsme-23.4R2.13.tgz kmdchk.log krt_rpf_filter.txt mmcq_authd mmcq_bbeStatsdGetCollector mmcq_mmdb_rep_mmcq mmcq_sdb_bbe_mmcq nsd_restart pfe-limit pfe_debug_commands phone-home/ pics/ policy_status rtsdb/ sd-upgrade/ sec-download/ vi.recover/ |
MD5 Check
| root> file checksum md5 /cf/var/tmp/junos-srxsme-23.4R2.13.tgz MD5 (/cf/var/tmp/junos-srxsme-23.4R2.13.tgz) = 18085ebeec8305f538226bd690b18954 |
Firmware Upgrade and check version
| root> request system software add /cf/var/tmp/junos-srxsme-23.4R2.13.tgz no-validate reboot 부팅 과정 생략 root> show version Model: srx320 Junos: 23.4R2.13 JUNOS Software Release [23.4R2.13] root> show system license License usage: Licensed Licensed Licensed Feature Feature Feature Feature name used installed needed Expiry idp-sig 0 1 0 2030-01-26 00:00:00 UTC remote-access-ipsec-vpn-client 0 2 0 permanent remote-access-juniper-std 0 2 0 permanent Licenses installed: License identifier: License version: 4 Valid for device: Customer ID: Features: idp-sig - IDP Signature date-based, 2024-12-27 00:00:00 UTC - 2030-01-26 00:00:00 UTC root> |
지금까지 [2025][Juniper SRX #29] Firmware Upgrade - CLI 글을 읽어주셔서 감사합니다.
'JUNIPER > SRX 방화벽' 카테고리의 다른 글
| [2025][Juniper SRX #31] Traffic Flow (0) | 2025.02.18 |
|---|---|
| [2025][Juniper SRX #30] IDP Signature Update (0) | 2025.02.16 |
| [2025][Juniper SRX #28] Destination Nat - DNAT (0) | 2025.02.16 |
| [2025][Juniper SRX #27] Destination Nat - Port Forwarding (0) | 2025.02.16 |
| [2025][Juniper SRX #27] Static NAT - One to One NAT (0) | 2025.02.14 |