안녕하세요.
오늘은 [2024][Juniper SRX #1] 기본 CLI 명령어를 확인해 보겠습니다.
1. Operational mode
아래처럼 hostname> 이 상태가 Operation mode입니다.
만약에 hostname이 vSRX이면 vSRX>으로 표시됩니다.
이 모드에서는 show, monitor, request 등 주로 설정값 등을 확인할 때 이 모드를 사용합니다.
| root> |
예를 들어 Interface 상태를 확인하고 싶을 경우
show interface terse
| root> show interfaces terse Interface Admin Link Proto Local Remote ge-0/0/0 up up gr-0/0/0 up up ip-0/0/0 up up lsq-0/0/0 up up lt-0/0/0 up up mt-0/0/0 up up sp-0/0/0 up up sp-0/0/0.0 up up inet inet6 sp-0/0/0.16383 up up inet ge-0/0/1 up up ge-0/0/2 up up dsc up up fti0 up up fxp0 up up fxp0.0 up up gre up up ipip up up irb up up lo0 up up lo0.16384 up up inet 127.0.0.1 --> 0/0 lo0.16385 up up inet 10.0.0.1 --> 0/0 10.0.0.16 --> 0/0 128.0.0.1 --> 0/0 128.0.0.4 --> 0/0 128.0.1.16 --> 0/0 lo0.32768 up up lsi up up mtun up up pimd up up pime up up pp0 up up ppd0 up up ppe0 up up st0 up up tap up up vlan up down root> |
2. configuration mode
이 모드로 들어가기 위해서는 아래처럼 operation mode에서 configure 명령어를 입력합니다.
root>에서 root# 바뀌었습니다. #의미가 configuration mode를 의미합니다.
이 모드에서는 edit, set, delete, activate 등의 명령어 사용가능
| root> configure Entering configuration mode [edit] root# |
만약에 configuration mode에서 operation mode에 있는 명령어를 사용하고 싶으면 run 명령어를 앞에 사용합니다.
| root# run show interfaces terse Interface Admin Link Proto Local Remote ge-0/0/0 up up gr-0/0/0 up up ip-0/0/0 up up lsq-0/0/0 up up lt-0/0/0 up up mt-0/0/0 up up sp-0/0/0 up up sp-0/0/0.0 up up inet inet6 sp-0/0/0.16383 up up inet ge-0/0/1 up up ge-0/0/2 up up dsc up up fti0 up up fxp0 up up fxp0.0 up up gre up up ipip up up irb up up lo0 up up lo0.16384 up up inet 127.0.0.1 --> 0/0 lo0.16385 up up inet 10.0.0.1 --> 0/0 10.0.0.16 --> 0/0 128.0.0.1 --> 0/0 128.0.0.4 --> 0/0 128.0.1.16 --> 0/0 lo0.32768 up up lsi up up mtun up up pimd up up pime up up pp0 up up ppd0 up up ppe0 up up st0 up up tap up up vlan up down [edit] root# |
3. 계층 간 이동 명령어
3-1 edit
3-2 top
3-3 up
3-4 exit
Juniper는 리눅스 기반에 동작하기 때문에 리눅스에 Statement Hierarchy 구조를 사용합니다.
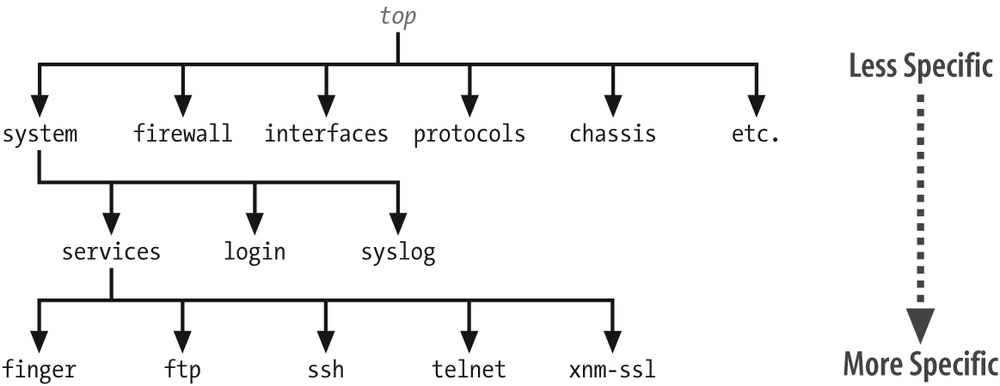
top 명령어
현재 interfaces 안에 있습니다. 이 상태에서 top명령어를 이용하고 최상으로 돌아갑니다.
최송이는 configuration mode입니다.
| root# edit interfaces [edit interfaces] root# top [edit] root# |
up 명령어
현재 system -> services -> ftp 위치에 있습니다.
up 명령어를 사용하면 바로 윗단계 services로 이동합니다.
| root# edit system services ftp [edit system services ftp] root# root# up [edit system services] root# |
만약에 2단계 위로 올라가고 싶으면 up 2 입력하면 됩니다.
| [edit system services ftp] root# up 2 [edit system] root# |
exit 명령어
한 단계 위로 이동 합니다.
또 configuration mode 최상위에서 exit 입력하면 operation mode로 진입합니다.
| root# edit system [edit system] root# root# exit [edit] root# root# exit Exiting configuration mode root> |
4. 명령어 단축키 사용방법
- Ctrl + p 또는 위 화살표키: 직전명령어호출
- Ctrl + n 또는 아래 화살표키 : 직전명령어 간 이동
- Ctrl + a, e : 명령어 제일 앞, 뒤으로 커서 이동
- Ctrl + w : 커서 앞 또는 커서가 위치한 단어 삭제
5. 설정 추가 삭제 명령어
set: 설정 추가 명령어
delete: 설정 삭제 명령어
set 명령어로 hostname를 설정해 보겠습니다.
주니퍼 디폴트 값으로 root 비밀번호가 없기 때문에 commit를 눌러서 변경값이 저장되지 않습니다.
우선 root password를 입력합니다.
set system root-authentication plain-text-password
그리고 호스트이름을 변경합니다
set system host-name vSRX
그리고 설정값을 저장 및 즉시 변경 합니다.
commit
Hostname이 바뀌었습니다.
| root> configure root# set system root-authentication plain-text-password New password: Retype new password: root# set system host-name vSRX [edit] root# commit commit complete [edit] root@vSRX# |
이번에는 delete 명령어를 사용해 보겠습니다.
set system services ftp 이 명령어를 삭제해 보겠습니다.
delete system services ftp
| root@vSRX> show configuration | display set | no-more set version 21.3R1.9 set system root-authentication encrypted-password "$6$L1Uj2iTj$/c8wM7UteO/L/q5NWbwvvTiYhwADjApBAJ7LQCQaZDVQfgwStnuOH36if38V.CMAxpr3Ia2Yyul0TGgHTdSbg/" set system services ftp set system services ssh set system services web-management http interface fxp0.0 set system services web-management https system-generated-certificate set system services web-management https interface fxp0.0 set system syslog file interactive-commands interactive-commands any set system syslog file messages any any set system syslog file messages authorization info set system license autoupdate url https://ae1.juniper.net/junos/key_retrieval set security screen ids-option untrust-screen icmp ping-death set security screen ids-option untrust-screen ip source-route-option set security screen ids-option untrust-screen ip tear-drop set security screen ids-option untrust-screen tcp syn-flood alarm-threshold 1024 set security screen ids-option untrust-screen tcp syn-flood attack-threshold 200 set security screen ids-option untrust-screen tcp syn-flood source-threshold 1024 set security screen ids-option untrust-screen tcp syn-flood destination-threshold 2048 set security screen ids-option untrust-screen tcp syn-flood queue-size 2000 set security screen ids-option untrust-screen tcp syn-flood timeout 20 set security screen ids-option untrust-screen tcp land set security policies from-zone trust to-zone trust policy default-permit match source-address any set security policies from-zone trust to-zone trust policy default-permit match destination-address any set security policies from-zone trust to-zone trust policy default-permit match application any set security policies from-zone trust to-zone trust policy default-permit then permit set security policies from-zone trust to-zone untrust policy default-permit match source-address any set security policies from-zone trust to-zone untrust policy default-permit match destination-address any set security policies from-zone trust to-zone untrust policy default-permit match application any set security policies from-zone trust to-zone untrust policy default-permit then permit set security policies pre-id-default-policy then log session-close set security zones security-zone trust tcp-rst set security zones security-zone untrust screen untrust-screen set interfaces fxp0 unit 0 root@vSRX> configure Entering configuration mode [edit] root@vSRX# delete system services ftp [edit] root@vSRX# commit commit complete [edit] root@vSRX# run show configuration | display set | match ftp [edit] root@vSRX# |
6. Pipe 명령어 사용 방법
- count : 표시되는 값의 라인 수를 출력함
- display : 설정값등을 보여주는 방식을 변경하여 표시
detail : 설정값에 주석으로 추가설정 가능한 예제를 표시
set : 설정값을 set형식으로 표시
xml : 설정값을 xml형식으로 표시
- except : 특정 값을 제외한 모든 값을 표시
- find : 특정값이 처음으로 시작되는 위치부터 표시
- match : 특정값이 포함된 값만 표시
- no-more : 표시내용이 한 페이지를 넘더라도 한 번에 모든 내용을 출력함
- hold : 표시내용이 한 페이지를 넘을 때 한 페이지단위로 표시하며 마지막에
--More-- 표시를 하지 않음
- save : 표시되는 값을 파일로 바로 저장 ex) show config | save 20120406.txt
- last : 표시내용의 마지막 부분을 표시 ex ) show log message | last 30(마지막 30라인만 출력)
- trim : 표시되는 값을 왼쪽을 기준으로 특정문자 수만큼 삭제하고 표시 * show log message Apr 6 15:55:22 SRX210 login: Login attempt for user stcon from host 1.1.1.100 * show log message | trim 15 (왼쪽기준으로 15자 삭제하고 출력) SRX210 login: Login attempt for user stcon from host 1.1.1.100
현재 juniper 방화벽 설정값 확인 하기
| root@vSRX> show configuration ## Last commit: 2024-06-09 12:47:19 UTC by root version 21.3R1.9; system { root-authentication { encrypted-password "$6$L1Uj2iTj$/c8wM7UteO/L/q5NWbwvvTiYhwADjApBAJ7LQCQaZDVQfgwStnuOH36if38V.CMAxpr3Ia2Yyul0TGgHTdSbg/"; ## SECRET-DATA } services { ssh; web-management { http { interface fxp0.0; } https { system-generated-certificate; interface fxp0.0; } } } syslog { file interactive-commands { interactive-commands any; } file messages { any any; authorization info; } } license { autoupdate { url https://ae1.juniper.net/junos/key_retrieval; } } } security { screen { ids-option untrust-screen { icmp { ping-death; } ip { source-route-option; tear-drop; } tcp { syn-flood { alarm-threshold 1024; attack-threshold 200; source-threshold 1024; destination-threshold 2048; queue-size 2000; ## Warning: 'queue-size' is deprecated timeout 20; } land; } } } policies { from-zone trust to-zone trust { policy default-permit { match { source-address any; destination-address any; application any; } then { permit; } } } from-zone trust to-zone untrust { policy default-permit { match { source-address any; destination-address any; application any; } then { permit; } } } pre-id-default-policy { then { log { session-close; } } } } zones { security-zone trust { tcp-rst; } security-zone untrust { screen untrust-screen; } } } interfaces { fxp0 { unit 0; } } root@vSRX> |
set 방식으로 설정값 표시 하기
show configuration | dispaly set
| root@vSRX> show configuration | display set set version 21.3R1.9 set system root-authentication encrypted-password "$6$L1Uj2iTj$/c8wM7UteO/L/q5NWbwvvTiYhwADjApBAJ7LQCQaZDVQfgwStnuOH36if38V.CMAxpr3Ia2Yyul0TGgHTdSbg/" set system services ssh set system services web-management http interface fxp0.0 set system services web-management https system-generated-certificate set system services web-management https interface fxp0.0 set system syslog file interactive-commands interactive-commands any set system syslog file messages any any set system syslog file messages authorization info set system license autoupdate url https://ae1.juniper.net/junos/key_retrieval set security screen ids-option untrust-screen icmp ping-death set security screen ids-option untrust-screen ip source-route-option set security screen ids-option untrust-screen ip tear-drop set security screen ids-option untrust-screen tcp syn-flood alarm-threshold 1024 set security screen ids-option untrust-screen tcp syn-flood attack-threshold 200 set security screen ids-option untrust-screen tcp syn-flood source-threshold 1024 set security screen ids-option untrust-screen tcp syn-flood destination-threshold 2048 set security screen ids-option untrust-screen tcp syn-flood queue-size 2000 set security screen ids-option untrust-screen tcp syn-flood timeout 20 set security screen ids-option untrust-screen tcp land ---(more)--- |
위에 --(more)-- 표시 없이 한꺼번에 output 표시하기.
| root@vSRX> show configuration | display set | no-more set version 21.3R1.9 set system root-authentication encrypted-password "$6$L1Uj2iTj$/c8wM7UteO/L/q5NWbwvvTiYhwADjApBAJ7LQCQaZDVQfgwStnuOH36if38V.CMAxpr3Ia2Yyul0TGgHTdSbg/" set system services ssh set system services web-management http interface fxp0.0 set system services web-management https system-generated-certificate set system services web-management https interface fxp0.0 set system syslog file interactive-commands interactive-commands any set system syslog file messages any any set system syslog file messages authorization info set system license autoupdate url https://ae1.juniper.net/junos/key_retrieval set security screen ids-option untrust-screen icmp ping-death set security screen ids-option untrust-screen ip source-route-option set security screen ids-option untrust-screen ip tear-drop set security screen ids-option untrust-screen tcp syn-flood alarm-threshold 1024 set security screen ids-option untrust-screen tcp syn-flood attack-threshold 200 set security screen ids-option untrust-screen tcp syn-flood source-threshold 1024 set security screen ids-option untrust-screen tcp syn-flood destination-threshold 2048 set security screen ids-option untrust-screen tcp syn-flood queue-size 2000 set security screen ids-option untrust-screen tcp syn-flood timeout 20 set security screen ids-option untrust-screen tcp land set security policies from-zone trust to-zone trust policy default-permit match source-address any set security policies from-zone trust to-zone trust policy default-permit match destination-address any set security policies from-zone trust to-zone trust policy default-permit match application any set security policies from-zone trust to-zone trust policy default-permit then permit set security policies from-zone trust to-zone untrust policy default-permit match source-address any set security policies from-zone trust to-zone untrust policy default-permit match destination-address any set security policies from-zone trust to-zone untrust policy default-permit match application any set security policies from-zone trust to-zone untrust policy default-permit then permit set security policies pre-id-default-policy then log session-close set security zones security-zone trust tcp-rst set security zones security-zone untrust screen untrust-screen set interfaces fxp0 unit 0 |
- find 명령어 - 특정값이 처음으로 시작되는 위치부터 추력
위에 설정값에서 policies 줄이 있는 곳부터 끝까지 출력해 보겠습니다.
| root@vSRX> show configuration | display set | find policies set security policies from-zone trust to-zone trust policy default-permit match source-address any set security policies from-zone trust to-zone trust policy default-permit match destination-address any set security policies from-zone trust to-zone trust policy default-permit match application any set security policies from-zone trust to-zone trust policy default-permit then permit set security policies from-zone trust to-zone untrust policy default-permit match source-address any set security policies from-zone trust to-zone untrust policy default-permit match destination-address any set security policies from-zone trust to-zone untrust policy default-permit match application any set security policies from-zone trust to-zone untrust policy default-permit then permit set security policies pre-id-default-policy then log session-close set security zones security-zone trust tcp-rst set security zones security-zone untrust screen untrust-screen set interfaces fxp0 unit 0 |
- match 특정값이 포함된 값만 표시해 보겠습니다
zones이라는 단어가 있는 줄만 표시해 보겠습니다.
| root@vSRX> show configuration | display set | match zones set security zones security-zone trust tcp-rst set security zones security-zone untrust screen untrust-screen root@vSRX> |
- except: 특정 값을 제외한 모든 값을 표시합니다.
zones이라는 단어가 있는 줄을 제외하고 출력해 보겠습니다
| root@vSRX> show configuration | display set | except zones set version 21.3R1.9 set system root-authentication encrypted-password "$6$L1Uj2iTj$/c8wM7UteO/L/q5NWbwvvTiYhwADjApBAJ7LQCQaZDVQfgwStnuOH36if38V.CMAxpr3Ia2Yyul0TGgHTdSbg/" set system services ssh set system services web-management http interface fxp0.0 set system services web-management https system-generated-certificate set system services web-management https interface fxp0.0 set system syslog file interactive-commands interactive-commands any set system syslog file messages any any set system syslog file messages authorization info set system license autoupdate url https://ae1.juniper.net/junos/key_retrieval set security screen ids-option untrust-screen icmp ping-death set security screen ids-option untrust-screen ip source-route-option set security screen ids-option untrust-screen ip tear-drop set security screen ids-option untrust-screen tcp syn-flood alarm-threshold 1024 set security screen ids-option untrust-screen tcp syn-flood attack-threshold 200 set security screen ids-option untrust-screen tcp syn-flood source-threshold 1024 set security screen ids-option untrust-screen tcp syn-flood destination-threshold 2048 set security screen ids-option untrust-screen tcp syn-flood queue-size 2000 set security screen ids-option untrust-screen tcp syn-flood timeout 20 set security screen ids-option untrust-screen tcp land set security policies from-zone trust to-zone trust policy default-permit match source-address any set security policies from-zone trust to-zone trust policy default-permit match destination-address any set security policies from-zone trust to-zone trust policy default-permit match application any set security policies from-zone trust to-zone trust policy default-permit then permit set security policies from-zone trust to-zone untrust policy default-permit match source-address any set security policies from-zone trust to-zone untrust policy default-permit match destination-address any set security policies from-zone trust to-zone untrust policy default-permit match application any set security policies from-zone trust to-zone untrust policy default-permit then permit set security policies pre-id-default-policy then log session-close set interfaces fxp0 unit 0 root@vSRX> |
save - 출력값을 파일로 저장하는 명령어입니다
설정값을 file로 저장해 보겠습니다.
file 이름은 config_backup입니다.
파일을 확인하기 위해서는 file list 명령어를 입력합니다.
| root@vSRX> show configuration | display set | save config_backup Wrote 32 lines of output to 'config_backup' root@vSRX> file list /root/: .cshrc@ -> /packages/mnt/os-runtime/root/.cshrc .login@ -> /packages/mnt/os-runtime/root/.login .profile@ -> /packages/mnt/os-runtime/root/.profile config_backup root@vSRX> |
파일 내용 확인하기
file show 파일 이름
root@vSRX> file show config_backup set version 21.3R1.9 set system root-authentication encrypted-password "$6$L1Uj2iTj$/c8wM7UteO/L/q5NWbwvvTiYhwADjApBAJ7LQCQaZDVQfgwStnuOH36if38V.CMAxpr3Ia2Yyul0TGgHTdSbg/" set system services ssh set system services web-management http interface fxp0.0 set system services web-management https system-generated-certificate set system services web-management https interface fxp0.0 set system syslog file interactive-commands interactive-commands any set system syslog file messages any any set system syslog file messages authorization info set system license autoupdate url https://ae1.juniper.net/junos/key_retrieval set security screen ids-option untrust-screen icmp ping-death set security screen ids-option untrust-screen ip source-route-option set security screen ids-option untrust-screen ip tear-drop set security screen ids-option untrust-screen tcp syn-flood alarm-threshold 1024 set security screen ids-option untrust-screen tcp syn-flood attack-threshold 200 set security screen ids-option untrust-screen tcp syn-flood source-threshold 1024 set security screen ids-option untrust-screen tcp syn-flood destination-threshold 2048 set security screen ids-option untrust-screen tcp syn-flood queue-size 2000 set security screen ids-option untrust-screen tcp syn-flood timeout 20 set security screen ids-option untrust-screen tcp land set security policies from-zone trust to-zone trust policy default-permit match source-address any set security policies from-zone trust to-zone trust policy default-permit match destination-address any set security policies from-zone trust to-zone trust policy default-permit match application any set security policies from-zone trust to-zone trust policy default-permit then permit set security policies from-zone trust to-zone untrust policy default-permit match source-address any set security policies from-zone trust to-zone untrust policy default-permit match destination-address any set security policies from-zone trust to-zone untrust policy default-permit match application any set security policies from-zone trust to-zone untrust policy default-permit then permit set security policies pre-id-default-policy then log session-close set security zones security-zone trust tcp-rst set security zones security-zone untrust screen untrust-screen set interfaces fxp0 unit 0 root@vSRX> |
last: 표시내용의 마지막 부분을 표시합니다.
ex) 로그에 마지막 10줄만 표시 - 즉 최신 로그 10개만 출력입니다.
| root@vSRX> show log messages | last 10 Jun 9 13:02:53 vSRX srxpfe[20805]: pconn_client_create: RE address for IRI1 1000080 cid is 0 Jun 9 13:03:05 vSRX last message repeated 4 times Jun 9 13:03:14 vSRX last message repeated 3 times Jun 9 13:03:17 vSRX mgd[23313]: UI_CMDLINE_READ_LINE: User 'root', command 'show log messages ' Jun 9 13:03:17 vSRX srxpfe[20805]: pconn_client_create: RE address for IRI1 1000080 cid is 0 Jun 9 13:03:35 vSRX last message repeated 6 times Jun 9 13:03:53 vSRX last message repeated 6 times Jun 9 13:03:55 vSRX mgd[23313]: UI_CMDLINE_READ_LINE: User 'root', command 'show log messages | last 10 ' root@vSRX> |
Pipe옵션은 중복에서도 사용 가능 합니다.
show log messages 출력
match VSRX 이 단어가 있는 messages만 출력
last 10 마지막으로부터 최신 10개 log만 출
| root@vSRX> show log messages | match VSRX | last 10 Jun 9 13:03:56 vSRX srxpfe[20805]: pconn_client_create: RE address for IRI1 1000080 cid is 0 Jun 9 13:04:06 vSRX last message repeated 3 times Jun 9 13:04:45 vSRX last message repeated 13 times Jun 9 13:04:47 vSRX mgd[23313]: UI_CMDLINE_READ_LINE: User 'root', command 'show log messages | match VSRX ' Jun 9 13:04:48 vSRX srxpfe[20805]: pconn_client_create: RE address for IRI1 1000080 cid is 0 Jun 9 13:04:51 vSRX srxpfe[20805]: pconn_client_create: RE address for IRI1 1000080 cid is 0 Jun 9 13:04:53 vSRX mgd[23313]: UI_CMDLINE_READ_LINE: User 'root', command 'show log messages | match VSRX | last 10 ' root@vSRX> |
?
입력하면 실행 가능한 명려어가 표시 됩니다.
| root@vSRX> ? Possible completions: clear Clear PPM related statistics information configure Manipulate software configuration information file Perform file operations help Provide help information load Load information from file monitor Show real-time debugging information mtrace Trace multicast path from source to receiver op Invoke an operation script ping Ping remote target probe Probe interfaces on remote target quit Exit the management session request Make system-level requests restart Restart software process scp Copy files via ssh set Set CLI properties, date/time, craft interface message show Show system information ssh Start secure shell on another host start Start shell telnet Telnet to another host test Perform diagnostic debugging traceroute |
지금까지 [2024][Juniper SRX #1] 기본 CLI 명령어 글을 읽어주셔서 감사합니다.
'JUNIPER > SRX 방화벽' 카테고리의 다른 글
| [2024][Juniper SRX #6] Interface 설정 - RVI - Trunk mode (1) | 2024.07.17 |
|---|---|
| [2024][Juniper SRX #5] Interface 설정 - RVI - access mode (1) | 2024.07.16 |
| [2024][Juniper SRX #4] Interface 설정 - Layer3 Logical Interface (0) | 2024.07.15 |
| [2024][Juniper SRX #3] Interface 설정 - Layer3 Physical Interface (0) | 2024.07.14 |
| [2024][Juniper SRX #2] Interface Numbering (0) | 2024.07.14 |